– 24 Hours Later: “Unprecedented” Fallout From “Biggest Ransomware Attack In History”:
24 hours after it first emerged, it has been called the first global, coordinated ransomware attack using hacking tools developed by the NSA, crippling over a dozen hospitals across the UK, mass transit around Europe, car factories in France and the UK, universities in China, corporations in the US, banks in Russia and countless other mission-critical businesses and infrastructure.
According to experts, “this could be one of the worst-ever recorded attacks of its kind.” The security researcher who tweets and blogs as MalwareTech told The Intercept, “I’ve never seen anything like this with ransomware,” and “the last worm of this degree I can remember is Conficker.” Conficker was a notorious Windows worm first spotted in 2008; it went on to infect over 9 million computers in nearly 200 countries.
The fallout, according to cyber-specialists, has been “unprecedented”: it has left unprepared governments, companies and security experts from China to the United Kingdom on Saturday reeling, and racing to contain the damage from the audacious cyberattack that spread quickly across the globe, raising fears that people would not be able to meet ransom demands before their data are destroyed.
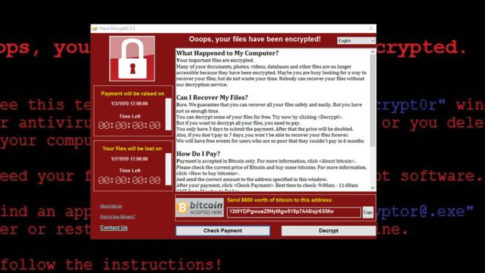
As reported yesterday, the global efforts come less than a day after malicious software, transmitted via email and stolen from the National Security Agency, exposed vulnerabilities in computer systems in almost 100 countries in one of the largest “ransomware” attacks on record. The cyberattackers took over the computers, encrypted the information on them and then demanded payment of $300 or more from users in the form of bitcoin to unlock the devices.
The ransomware was subsequently identified as a new variant of “WannaCry” that had the ability to automatically spread across large networks by exploiting a known bug in Microsoft’s Windows operating system.
The ransomware has been identifed as WannaCry
The hackers, who have not come forward to claim responsibility or otherwise been identified, likely made it a “worm”, or self spreading malware, by exploiting a piece of NSA code known as “Eternal Blue” that was released last month by a group known as the Shadow Brokers (see “Hacker Group Releases Password To NSA’s “Top Secret Arsenal” In Protest Of Trump Betrayal“) , researchers with several private cyber security firms said.
“This is one of the largest global ransomware attacks the cyber community has ever seen,” said Rich Barger, director of threat research with Splunk. The extremely well coordinated attack first emerged in the United Kingdom around noon on Friday and spread like wildefire around the globe. According to the Times “it has set off fears that the effects of the continuing threat will be felt for months, if not years” and raised questions about the intentions of the hackers: Did they carry out the attack for mere financial gain or for other unknown reasons?
The animated map below shows the speed and scale of the global infestation which took just a few hours to cover the globe:
Animated map of how tens of thousands of computers were infected with ransomware https://t.co/LDFCW9K5Lspic.twitter.com/E5Ep9KesaV
— The New York Times (@nytimes) May 13, 2017
Meanwhile, some of the world’s largest institutions and government agencies have been affected, including the Russian Interior Ministry, FedEx in the United States and Britain’s National Health Service. As people fretted over whether to pay the digital ransom or lose data from their computers, experts said the attackers might pocket more than $1 billion worldwide before the deadline ran out to unlock the machines.
Across Asia, several universities and organizations said they had been affected. In China, the virus hit the computer networks of both companies and universities, according to the state-run news media. News about the attack began trending on Chinese social media on Saturday, though most attention was focused on university networks, where there were concerns about students losing access to their academic work. The attack, however, focused on the UK and Europe where in addition to the British healthcare system, companies like Deutsche Bahn, the German transport giant; Telefónica, a Spanish telecommunications firm; and Renault, the French automaker, said some of their systems had been affected.
“Seeing a large telco like Telefonica get hit is going to get everybody worried,” said Chris Wysopal, chief technology officer with cyber security firm Veracode.
The British National Health Service said that 45 of its hospitals, doctors’ offices and ambulance companies had been crippled — making it perhaps one of the largest institutions affected worldwide. Surgical procedures were canceled and some hospital operations shut down as government officials struggled to respond to the attack.
“We are not able to tell you who is behind that attack,” Amber Rudd, Britain’s home secretary, told the British Broadcasting Corporation on Saturday. “That work is still ongoing.”
Things only got worse on Saturday as auto production facilities across Europe have been shuttered, including car plants in the UK and France, in the aftermath of the cyberattack.
#BREAKING Renault says production halted at French sites after cyberattack
— AFP news agency (@AFP) May 13, 2017
Sky News understands production at the Nissan factory in Sunderland has been affected as a result of a cyber attack
— Sky News Newsdesk (@SkyNewsBreak) May 13, 2017
In total, more than 75,000 computers in 99 countries were compromised in Friday’s attack, with a heavy concentration of infections in Russia and Ukraine, according to Dutch security company Avast Software BV. Russia’s Interior Ministry, with oversees the country’s police forces, said “around 1,000 computers were infected,” which it described as less than 1 percent of the total, the New York Times reported. The ministry said technicians had stopped the attack and were updating the department’s “antivirus defense systems,” according to the Times. Russia’s RIA reported that the central bank said on Saturday it had detected “massive” cyber attacks on domestic banks, which successfully thwarted them.
* * *
There has been some good news: an ingenious discovery appears to have halted the spread of the virus for now.
As part of the digital attack, the hackers included a way of disabling the malware in case they wanted to shut down their activities, Ars Technica reported. To do so, the assailants included code in the ransomware that would stop it from spreading if the virus sent an online request to a website created by the attackers. The kill switch would stop the malware from spreading as soon as the website went online and communicated with the spreading digital virus.
A British-based researcher, who declined to give his name, registered a
domain that he noticed the malware was trying to connect to, limiting
the worm’s spread. When the 22-year-old British researcher, whose Twitter handle is @MalwareTechBlog, confirmed his involvement but insisted on anonymity because he did not want the public scrutiny, saw that the kill switch’s domain name — a long and complicated set of letters — had yet to be registered, he bought it himself. By making the site go live, the researcher shut down the hacking attack before it could fully spread to the United States.However, this temporary workaround will only last for a few days if not hours.
“I will confess that I was unaware registering the domain would stop the malware until after I registered it, so initially it was accidental,” wrote the @MalwareTechBlog researcher. “So long as the domain isn’t revoked, this particular strain will no longer cause harm, but patch your systems ASAP as they will try again.”
I will confess that I was unaware registering the domain would stop the malware until after i registered it, so initially it was accidental.
— MalwareTech (@MalwareTechBlog) May 13, 2017
“The kill switch is why the U.S. hasn’t been touched so far,” said Matthieu Suiche, founder of Comae Technologies, a cybersecurity company in the United Arab Emirates. “But it’s only temporary. All the attackers would have to do is create a variant of the hack with a different domain name. I would expect them to do that.”
Adds Reuters: “We are on a downward slope, the infections are extremely few, because the malware is not able to connect to the registered domain,” said Vikram Thakur, principal research manager at Symantec.
“The numbers are extremely low and coming down fast.” But the attackers may yet tweak the code and restart the cycle. The British-based researcher who may have foiled the ransomware’s spread told Reuters he had not seen any such tweaks yet, “but they will.”
* * *
Meanwhile, questions are mounting why code created by the NSA. has i) fallen in the wrong hands and ii) is being used to hold the world hostage. As the NYT notes, the ability of the cyberattack to spread so quickly was partly because of its high level of sophistication.
The malware, experts said, was based on a method that the N.S.A. is believed to have developed as part of its arsenal of cyberweapons. Last summer, a group calling itself the “Shadow Brokers” posted online digital tools that it had stolen from the United States government’s stockpile of hacking weapons. The connection to the N.S.A. is likely to draw further criticism from privacy advocates who have repeatedly called for a clampdown on how the agency collects information online.
Brian Lord, a former deputy director for intelligence and cyber operations at Government Communications Headquarters, Britain’s equivalent to the N.S.A., said that any investigation, which would include the F.B.I. and the National Crime Agency of Britain, would take months to name the potential attackers, if it ever does. And by focusing the attacks on large institutions with a track record of not keeping their technology systems up-to-date, global criminal organizations were cherry-picking easy targets that were highly susceptible to such hacks, according to Mr. Lord.
“Serious organized crime is looking to these new technologies to the maximum effect,” Mr. Lord said. “With cybercrime, you can operate globally without leaving where you already are.”
He added of this attack: “It was well thought-out, well timed and well coordinated. But, fundamentally, there is nothing unusual about its delivery. It is still fundamentally robbery and extortion.”
For now, the victims – both actual and potential – may have bought themselves some time. As part of the efforts to combat the attack, Microsoft, whose Windows software lies at the heart of the potential hacking vulnerability, released a software update available to those affected by the attack and others who could be potential targets. Microsoft took the “highly unusual” step of securing early operating systems in the wake of a massive ransomware attack that wreaked havoc on global computer networks, including the UK’s National Health Service. Overnight, Microsoft XP received the new security patch three years after the computer giant discontinued support for the OS.
“Seeing businesses and individuals affected by cyberattacks, such as the ones reported today [Friday], was painful,” a Microsoft statement read. “We are taking the highly unusual step of providing a security update for all customers to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003.”
Security experts however said the upgrade came too late for many of the tens of thousands of machines that were locked out and whose data could be erased if people did not pay the ransom. Earlier this year, Microsoft created a patch called MS17-010 to guard against the virus. But older, unsupported operating systems were not included in the update.
Making matters worse, government officials and industry watchers also warned on Saturday that other hackers might now try to use the global ransomware attack for their own means, potentially tweaking the code and developing their own targets for new cyberattacks.
* * *
Finally, there is the question who is behind this coordinated global attack. Not surprisingly, Russia has been named. There is a high-probability that Russian-language cyber-criminals were behind the attack, said Aleks Gostev, chief cybersecurity expert for Kaspersky Labs. “Ransomware is traditionally their topic,” he said cited by Bloomberg. “The geography of attacks that hit post-Soviet Union most also suggests that.”
Whoever is the responsible party behind this first, global, coordinated ransomware attack, the have demonstrated one thing: the world is thoroughly unprepared for cyberwar.
“As with everything in cyber, we’re now waiting for the next type of attack,” Paul Bantick, a cyber security expert at Beazley, a global insurance underwriter, told the NYT.
“Ransomware like this has been on the rise over the last 18 months,” he added. “This represents the next step that people were expecting.”
As such, it is only a matter of time now before an even greater, more destructive cyberattack is unleashed on the world.
* * *
PayPal: Donate in USD
PayPal: Donate in EUR
PayPal: Donate in GBP
Man Sentenced To Prison By Proprietary Algorithm
http://news.filehippo.com/2017/05/man-sentenced-to-prison-by-proprietary-algorithm/
https://www.youtube.com/watch?v=9I9mp1JuPGA
Large group of black people raid a Washington D C 7 11 — AGAIN
https://www.youtube.com/watch?v=hEbcYP5o_e0
We Found Another State of Matter: The Supersolid!